© 2025 EAMC – Managed. Secured. Assured. All rights reserved.
In today’s fast-evolving technological landscape, organizations need more than just IT infrastructure; they need an integrated, forward-thinking approach that aligns business goals with technical capabilities. EAMC’s Enterprise Architecture (EA) Solutions are designed to provide a structured framework for transforming complex systems into cohesive, agile, and scalable environments that drive organizational success.
We ensure that IT investments and business strategies move in tandem, creating an architecture that supports both current and future goals. Through careful alignment, EAMC enables your organization to leverage technology as a powerful tool for sustainable growth.
EAMC’s EA approach standardizes processes, data, and technology, reducing redundancy and streamlining operations. Our tailored solutions optimizing resource utilization, minimizing operational costs, and ensuring scalability across all functions.
With EAMC, organizations are equipped to handle compliance requirements and manage risks effectively. Our EA solutions include robust frameworks that identify and mitigate technology-related risks, from cybersecurity threats to regulatory obligations, ensuring a resilient operational environment.
At EAMC, we simplify the complexity of multi-system environments by enhancing interoperability, ensuring seamless integration, and enabling exchange across platforms. Our solutions support cohesive workflows that improve productivity andenhance collaboration.
EAMC’s EA solutions foster an adaptable IT landscape that supports continuous innovation. We provide a foundation that allows for the rapid adoption of emergingtechnologies, enabling your organization to stay ahead in a competitive market.
Whether you’re seeking to refine your IT framework or undertake a full-scale digital transformation, EAMC’s Enterprise Architecture Solutions offer the structure and insight needed to achieve your objectives. With a focus on people, processes, and technology, we empower your organization to operate with clarity, efficiency, and resilience.
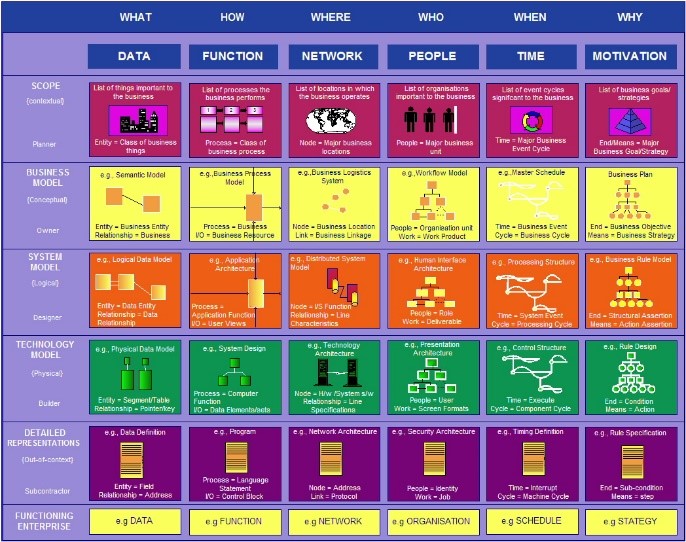
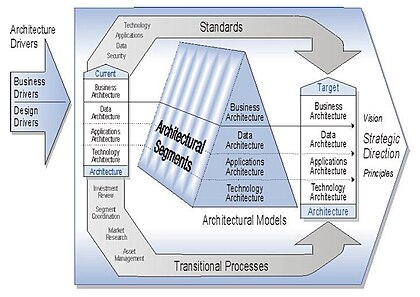
The Zachman Framework organizes enterprise architecture using a Two-Dimensional Classification Schema, with six interrogatives (What, How, When, Who, Where, Why) in a 6x6 Matrix Structure. It serves as an Enterprise Ontology, defining essential components, but is Not a Methodology, focusing on structuring architectural artifacts rather than guiding implementations.
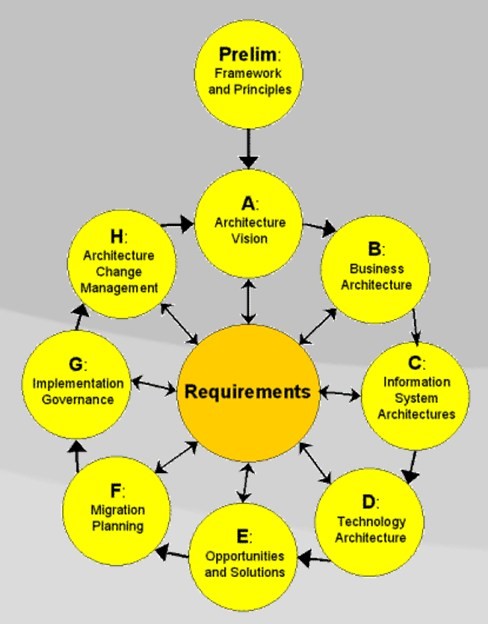
TOGAF (The Open Group Architecture Framework) is a globally recognized enterprise architecture credential. It provides a structured approach to designing, planning, implementing, and governing IT architecture. TOGAF follows a high-level design approach, modeled at four levels: Business, Application, Data, and Technology, emphasizing modularization, standardization, and leveraging proven technologies and products.
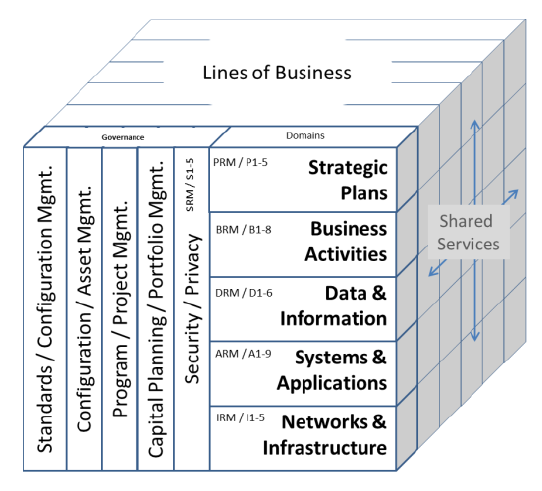
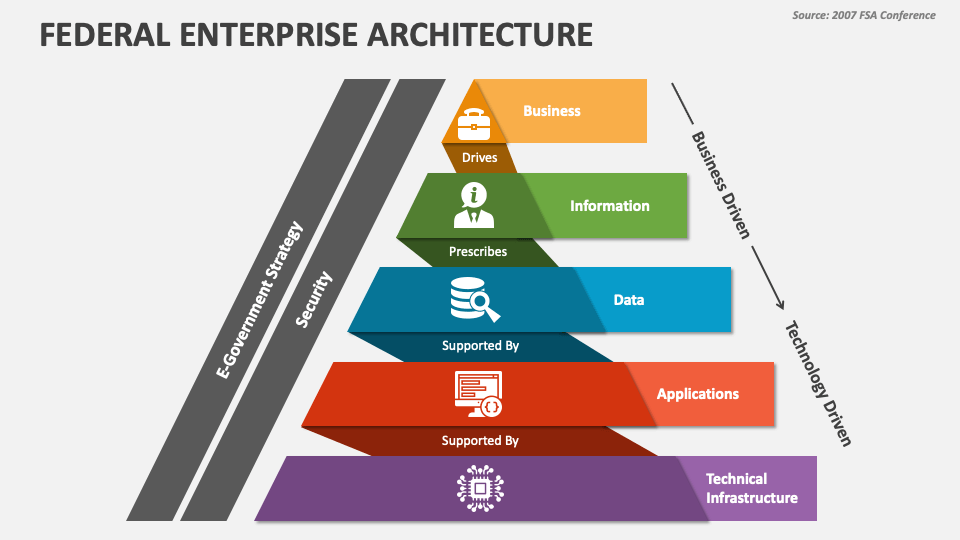
Enterprise architecture consists of four key components: Business Architecture, defining roles, processes, and objectives; Data Architecture, managing the information used for operations; Application Architecture, overseeing software applications processing data; and Technology Architecture, supporting all layers with hardware and communication technology. Together, these components ensure efficient, structured, and scalable business operations.
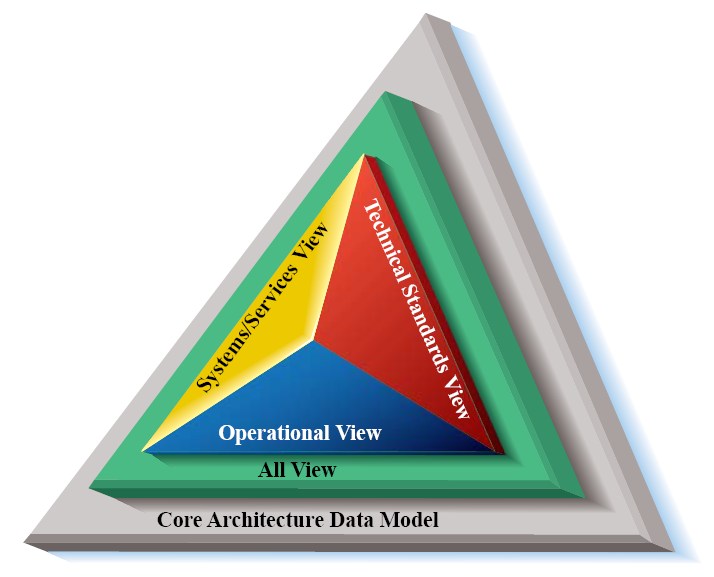
The Department of Defense Architecture Framework (DODAF) is a comprehensive framework used by the U.S. DoD to develop and manage enterprise architectures. It provides a structured approach for representing and visualizing DoD systems, ensuring all stakeholders have a clear, consistent understanding of system structure and behavior for effective decision-making and operations.
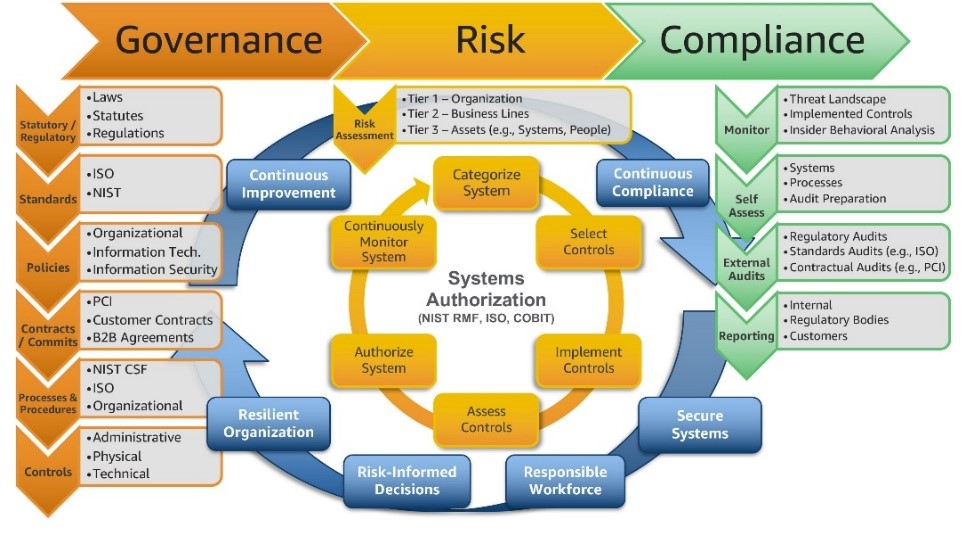
Governance, Risk, and Compliance (GRC) is a structured approach aligning IT and business goals while managing risks and meeting regulations. Governance sets policies and accountability, risk management identifies and mitigates threats, and compliance ensures adherence to laws. Integrating these enhances decision-making, efficiency, and business continuity while minimizing risks and regulatory issues.

The Risk Management Framework (RMF) integrates security, privacy, and cyber supply chain risk management into the system development life cycle. It follows a risk-based approach to control selection, considering legal, policy, and regulatory constraints. RMF applies to new and legacy systems across all technologies and organizations, ensuring effective information security and privacy management.
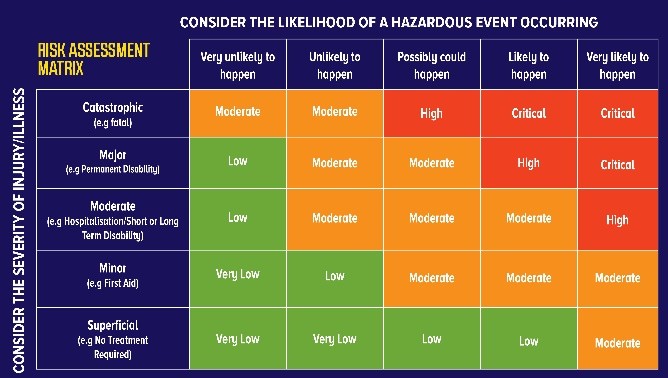
A risk assessment evaluates the likelihood, consequences, and tolerances of potential incidents. As part of a broader risk management strategy, it introduces control measures to mitigate risks. Its primary goal is to prevent negative outcomes or identify potential opportunities, ensuring effective decision-making and improved organizational resilience against uncertainties.
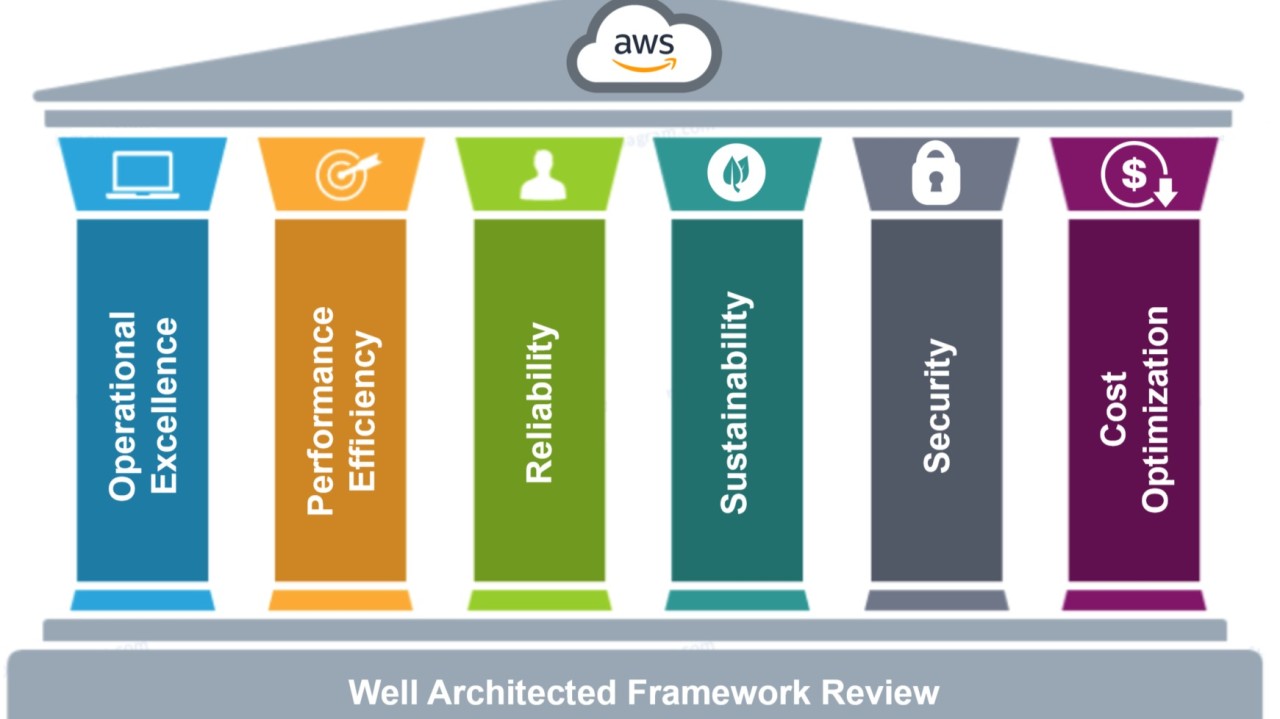
The AWS Well-Architected Framework helps assess whether a specific architecture aligns with cloud best practices. It provides a consistent approach to evaluating systems based on modern cloud standards and identifies necessary improvements. As AWS evolves, the framework is continually refined to incorporate learnings from customer experiences and advancements in cloud technology.
The Modernizing Government Technology (MGT) Act is a new federal act that mandates federal agencies to accelerate their IT modernization efforts. The act allows agencies to reprogram unused budget allocation to fund future IT modernization projects. It also updates the uses of the Technology Modernization Fund (TMF) to pay for retiring and replacing older information technology (IT) systems.
The Modernizing Government Technology Act reforms and reauthorizes the Technology Modernization Fund (TMF) and its governing board, the Technology Modernization Board (TMB), which were established by the bipartisan Modernizing Government Technology Act of 2017 (P.L. 115-91). The bill includes several measures to improve the administration of the TMF and ensure program operations adhere to original congressional intent. The bill requires TMF awards to be reimbursed at the level needed to ensure the Fund is operational and creates a new requirement that agency’s reimburse administrative fees. The bill also establishes a Federal Legacy IT Inventory, a new oversight tool that will allow Congress to evaluate agency and government-wide priority items for legacy IT modernization and to assess how well the TMF does in funding these projects. Finally, this bill reauthorizes the TMF and TMB and establishes a December 2031 sunset.
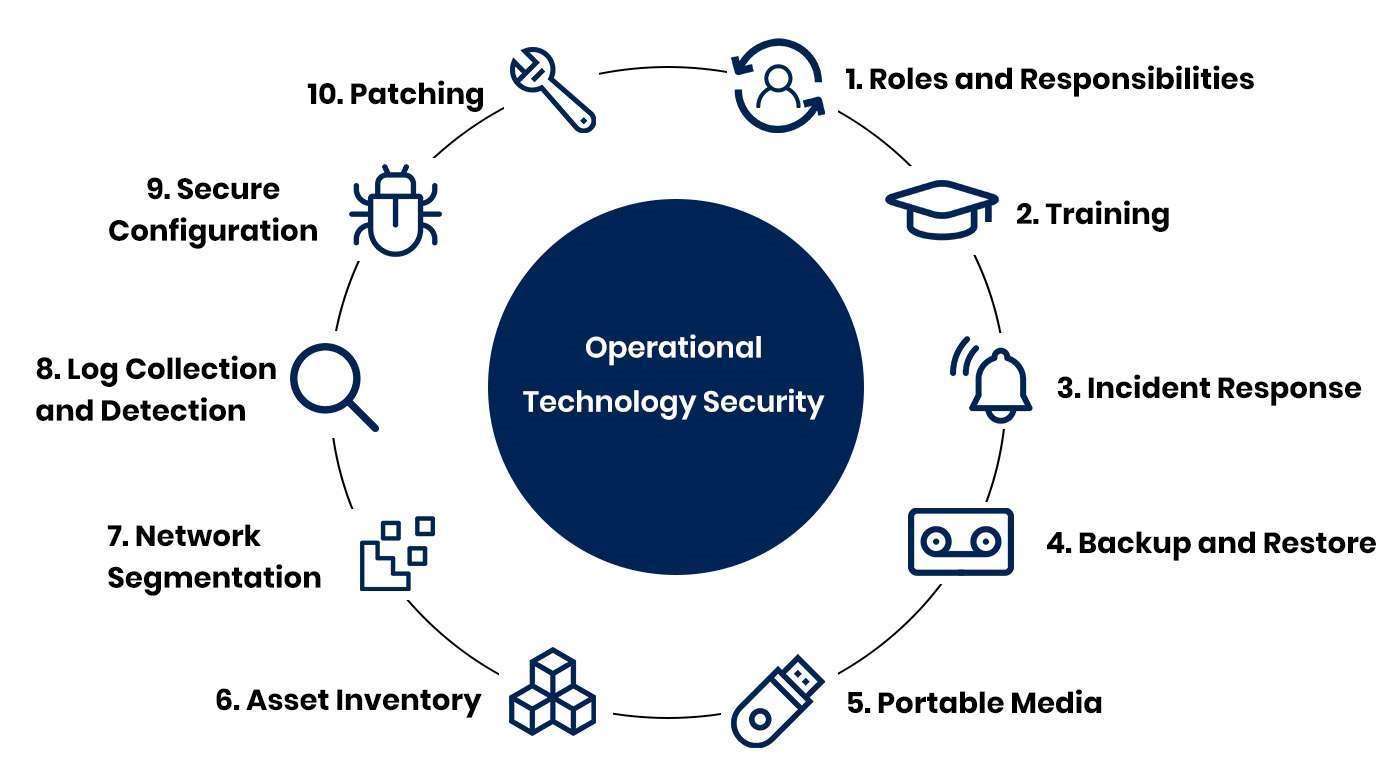
Operational Technology (OT) cybersecurity focuses on protecting the hardware and software that manage and control physical devices and processes in industrial environments.
Key aspects of OT cybersecurity include:
Transform data into actionable insights with advanced analytics and data governance solutions that drive informed decision-making.
An enterprise data architecture framework (EDAF) is a structured approach to managing and organizing data within an organization. It encompasses the entire data lifecycle, from collection and storage to processing and analysis.

FISMA compliance refers to adhering to a set of policies, standards, and guidelines to protect government information and systems. It is mandatory for federal agencies and their contractors. The key steps to achieve FISMA compliance include:
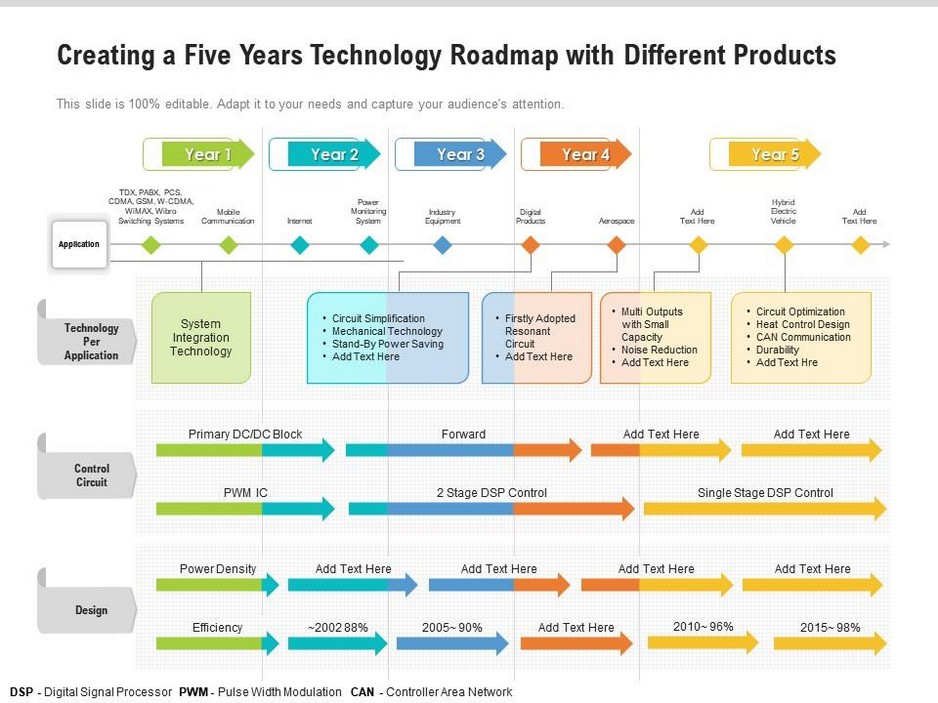
A Technology Roadmap is a strategic plan that outlines the technology initiatives an organization plans to undertake over a specific timeframe. It helps align technology projects with business goals, ensuring that all stakeholders understand the “what”, “why”, and “when” of IT initiatives.
Here are some key benefits of a Technology Roadmap:
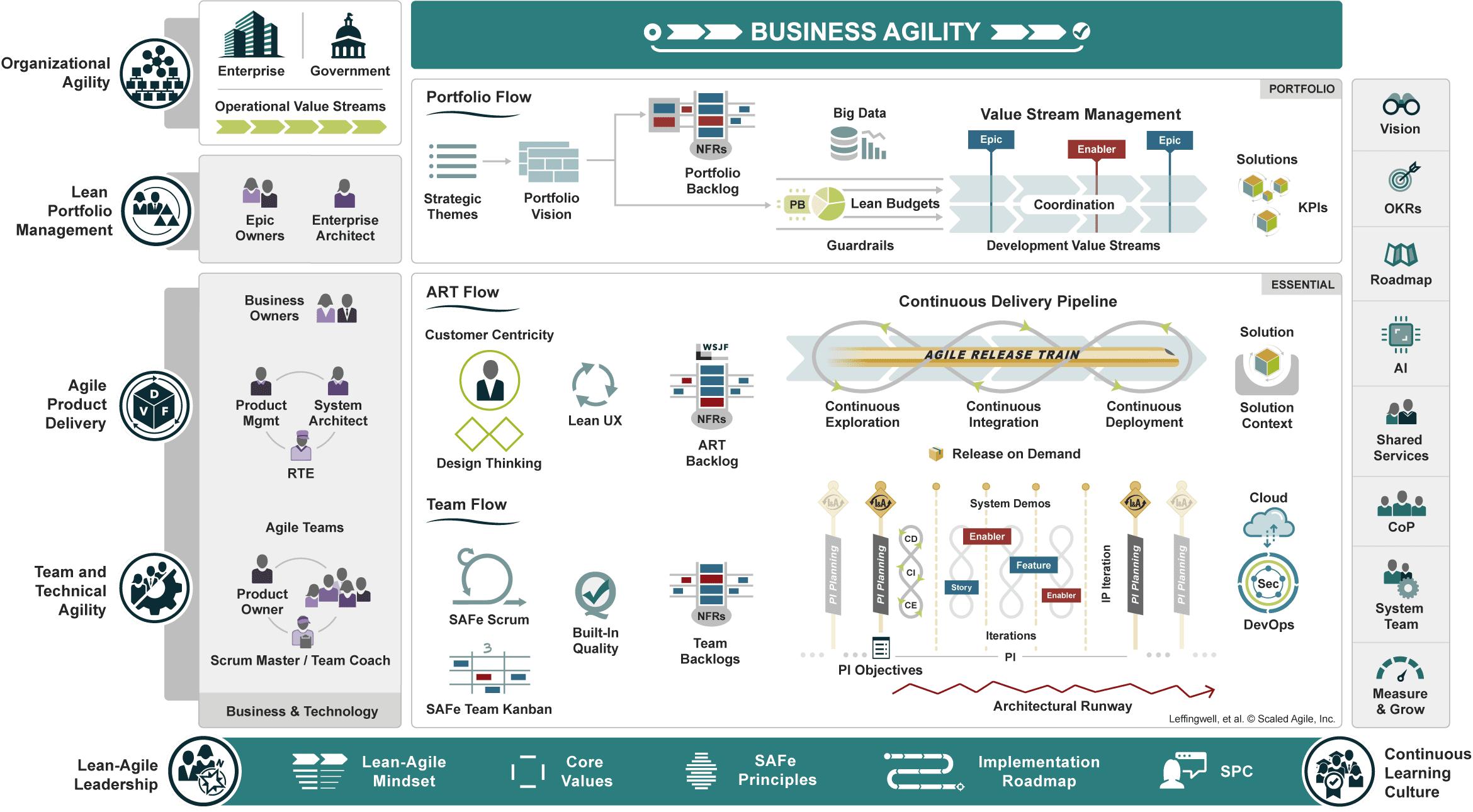
Product vision – Describes the desired future state of the product and guides Agile ARTs and teams toward a common goal.
Product strategy – Defines how the organization will deliver against the product vision, providing clear direction while retaining the agility needed to evolve based on feedback and market conditions.
Product design – Combines customer centricity, design thinking, and lean user experience (lean UX) design to understand the problem to be solved deeply and discover solutions with the best product-market fit.
Product delivery – Accelerates value realization by ensuring that new ideas flow quickly from idea to impact through a Continuous Delivery Pipeline.
Product marketing – Raises awareness and excitement in the market by amplifying the features and benefits of product innovations.
Product innovation culture – Fosters continuous learning, experimentation, and a spirit of relentless improvement across the organization.
© Scaled Agile, Inc.
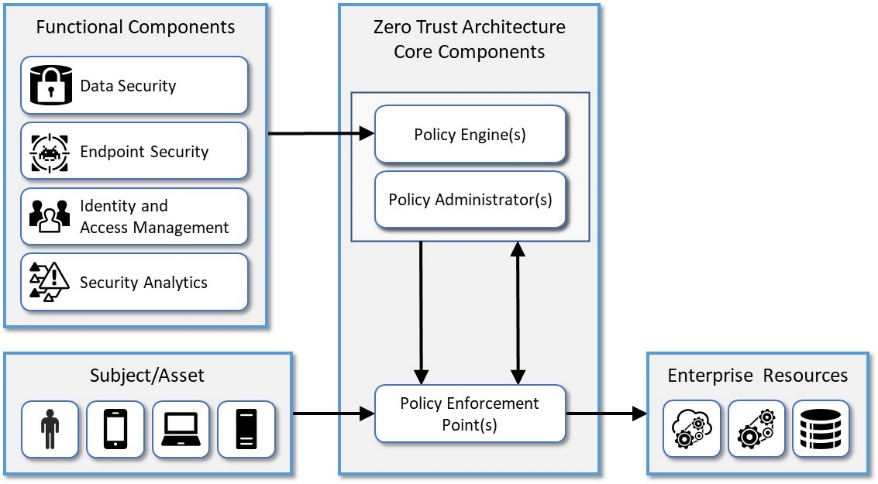
The NIST Zero Trust Architecture (ZTA) is a cybersecurity framework that emphasizes the principle of "never trust, always verify." It focuses on securing resources, users, and assets by assuming no implicit trust based on network location or ownership. You can explore the official NIST publication on Zero Trust Architecture here. Additionally, you might find a detailed guide and diagram in the NIST Special Publication 800-207.

The Zachman Framework organizes enterprise architecture using a Two-Dimensional Classification Schema, with six interrogatives (What, How, When, Who, Where, Why) in a 6x6 Matrix Structure. It serves as an Enterprise Ontology, defining essential components, but is Not a Methodology, focusing on structuring architectural artifacts rather than guiding implementations.

TOGAF (The Open Group Architecture Framework) is a globally recognized enterprise architecture credential. It provides a structured approach to designing, planning, implementing, and governing IT architecture. TOGAF follows a high-level design approach, modeled at four levels: Business, Application, Data, and Technology, emphasizing modularization, standardization, and leveraging proven technologies and products.

Enterprise architecture consists of four key components: Business Architecture, defining roles, processes, and objectives; Data Architecture, managing the information used for operations; Application Architecture, overseeing software applications processing data; and Technology Architecture, supporting all layers with hardware and communication technology. Together, these components ensure efficient, structured, and scalable business operations.

The Department of Defense Architecture Framework (DODAF) is a comprehensive framework used by the U.S. DoD to develop and manage enterprise architectures. It provides a structured approach for representing and visualizing DoD systems, ensuring all stakeholders have a clear, consistent understanding of system structure and behavior for effective decision-making and operations.

Governance, Risk, and Compliance (GRC) is a structured approach aligning IT and business goals while managing risks and meeting regulations. Governance sets policies and accountability, risk management identifies and mitigates threats, and compliance ensures adherence to laws. Integrating these enhances decision-making, efficiency, and business continuity while minimizing risks and regulatory issues.

The Risk Management Framework (RMF) integrates security, privacy, and cyber supply chain risk management into the system development life cycle. It follows a risk-based approach to control selection, considering legal, policy, and regulatory constraints. RMF applies to new and legacy systems across all technologies and organizations, ensuring effective information security and privacy management.

A risk assessment evaluates the likelihood, consequences, and tolerances of potential incidents. As part of a broader risk management strategy, it introduces control measures to mitigate risks. Its primary goal is to prevent negative outcomes or identify potential opportunities, ensuring effective decision-making and improved organizational resilience against uncertainties.

The AWS Well-Architected Framework helps assess whether a specific architecture aligns with cloud best practices. It provides a consistent approach to evaluating systems based on modern cloud standards and identifies necessary improvements. As AWS evolves, the framework is continually refined to incorporate learnings from customer experiences and advancements in cloud technology.

The Modernizing Government Technology (MGT) Act is a new federal act that mandates federal agencies to accelerate their IT modernization efforts. The act allows agencies to reprogram unused budget allocation to fund future IT modernization projects. It also updates the uses of the Technology Modernization Fund (TMF) to pay for retiring and replacing older information technology (IT) systems.

The Modernizing Government Technology Act reforms and reauthorizes the Technology Modernization Fund (TMF) and its governing board, the Technology Modernization Board (TMB), which were established by the bipartisan Modernizing Government Technology Act of 2017 (P.L. 115-91). The bill includes several measures to improve the administration of the TMF and ensure program operations adhere to original congressional intent. The bill requires TMF awards to be reimbursed at the level needed to ensure the Fund is operational and creates a new requirement that agency’s reimburse administrative fees. The bill also establishes a Federal Legacy IT Inventory, a new oversight tool that will allow Congress to evaluate agency and government-wide priority items for legacy IT modernization and to assess how well the TMF does in funding these projects. Finally, this bill reauthorizes the TMF and TMB and establishes a December 2031 sunset.

Operational Technology (OT) cybersecurity focuses on protecting the hardware and software that manage and control physical devices and processes in industrial environments.
Key aspects of OT cybersecurity include:

Transform data into actionable insights with advanced analytics and data governance solutions that drive informed decision-making.
An enterprise data architecture framework (EDAF) is a structured approach to managing and organizing data within an organization. It encompasses the entire data lifecycle, from collection and storage to processing and analysis.

FISMA compliance refers to adhering to a set of policies, standards, and guidelines to protect government information and systems. It is mandatory for federal agencies and their contractors. The key steps to achieve FISMA compliance include:

A Technology Roadmap is a strategic plan that outlines the technology initiatives an organization plans to undertake over a specific timeframe. It helps align technology projects with business goals, ensuring that all stakeholders understand the “what”, “why”, and “when” of IT initiatives.
Here are some key benefits of a Technology Roadmap:

Product vision – Describes the desired future state of the product and guides Agile ARTs and teams toward a common goal.
Product strategy – Defines how the organization will deliver against the product vision, providing clear direction while retaining the agility needed to evolve based on feedback and market conditions.
Product design – Combines customer centricity, design thinking, and lean user experience (lean UX) design to understand the problem to be solved deeply and discover solutions with the best product-market fit.
Product delivery – Accelerates value realization by ensuring that new ideas flow quickly from idea to impact through a Continuous Delivery Pipeline.
Product marketing – Raises awareness and excitement in the market by amplifying the features and benefits of product innovations.
Product innovation culture – Fosters continuous learning, experimentation, and a spirit of relentless improvement across the organization.
© Scaled Agile, Inc.

The NIST Zero Trust Architecture (ZTA) is a cybersecurity framework that emphasizes the principle of "never trust, always verify." It focuses on securing resources, users, and assets by assuming no implicit trust based on network location or ownership. You can explore the official NIST publication on Zero Trust Architecture here. Additionally, you might find a detailed guide and diagram in the NIST Special Publication 800-207.
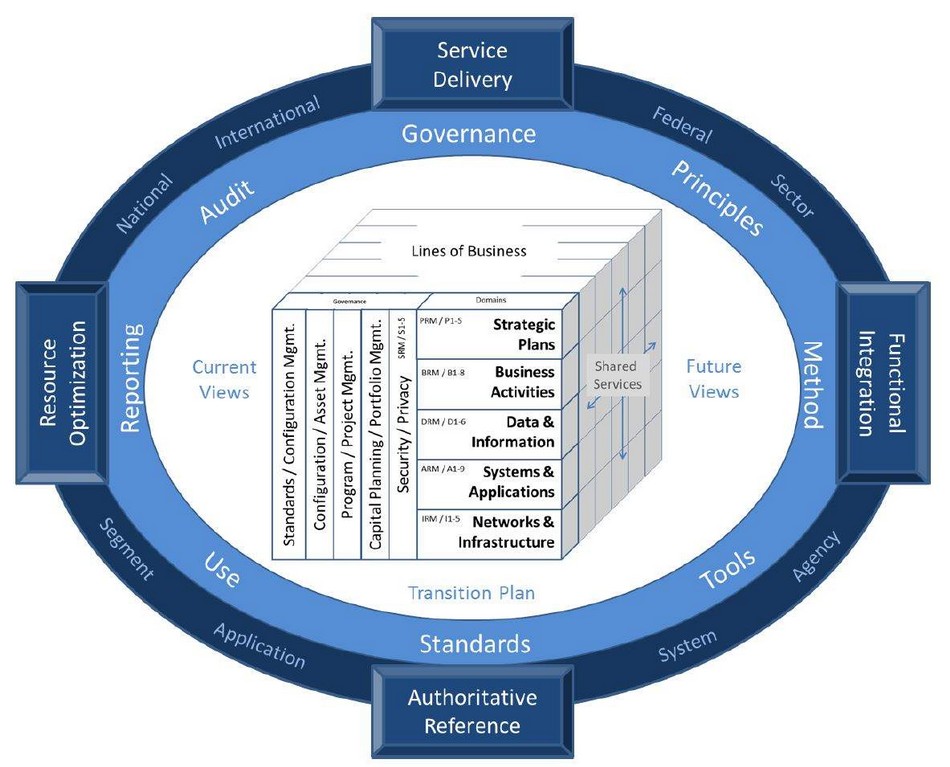
At EAMC, our certified Enterprise Architecture (EA) professionals bring clarity to complexity by leveraging proven frameworks such as TOGAF, DoDAF, FEAF, and Zachman. Our EA Solutions Practice helps organizations modernize and align their technology environments with mission and business objectives. We design scalable, secure, and future-ready architectures that reduce operational risk, improve agility, and accelerate digital transformation. With a commitment to sustainable growth and innovation, EAMC turns enterprise strategy into actionable results delivering strong architectural foundations that drive performance and resilience.

The Zachman Framework organizes enterprise architecture using a Two-Dimensional Classification Schema, with six interrogatives (What, How, When, Who, Where, Why) in a 6x6 Matrix Structure. It serves as an Enterprise Ontology, defining essential components, but is Not a Methodology, focusing on structuring architectural artifacts rather than guiding implementations.

TOGAF (The Open Group Architecture Framework) is a globally recognized enterprise architecture credential. It provides a structured approach to designing, planning, implementing, and governing IT architecture. TOGAF follows a high-level design approach, modeled at four levels: Business, Application, Data, and Technology, emphasizing modularization, standardization, and leveraging proven technologies and products.

Enterprise architecture consists of four key components: Business Architecture, defining roles, processes, and objectives; Data Architecture, managing the information used for operations; Application Architecture, overseeing software applications processing data; and Technology Architecture, supporting all layers with hardware and communication technology. Together, these components ensure efficient, structured, and scalable business operations.

The Department of Defense Architecture Framework (DODAF) is a comprehensive framework used by the U.S. DoD to develop and manage enterprise architectures. It provides a structured approach for representing and visualizing DoD systems, ensuring all stakeholders have a clear, consistent understanding of system structure and behavior for effective decision-making and operations.

The Zachman Framework organizes enterprise architecture using a Two-Dimensional Classification Schema, with six interrogatives (What, How, When, Who, Where, Why) in a 6x6 Matrix Structure. It serves as an Enterprise Ontology, defining essential components, but is Not a Methodology, focusing on structuring architectural artifacts rather than guiding implementations.

TOGAF (The Open Group Architecture Framework) is a globally recognized enterprise architecture credential. It provides a structured approach to designing, planning, implementing, and governing IT architecture. TOGAF follows a high-level design approach, modeled at four levels: Business, Application, Data, and Technology, emphasizing modularization, standardization, and leveraging proven technologies and products.

Enterprise architecture consists of four key components: Business Architecture, defining roles, processes, and objectives; Data Architecture, managing the information used for operations; Application Architecture, overseeing software applications processing data; and Technology Architecture, supporting all layers with hardware and communication technology. Together, these components ensure efficient, structured, and scalable business operations.

The Department of Defense Architecture Framework (DODAF) is a comprehensive framework used by the U.S. DoD to develop and manage enterprise architectures. It provides a structured approach for representing and visualizing DoD systems, ensuring all stakeholders have a clear, consistent understanding of system structure and behavior for effective decision-making and operations.

Governance, Risk, and Compliance (GRC) is a structured approach aligning IT and business goals while managing risks and meeting regulations. Governance sets policies and accountability, risk management identifies and mitigates threats, and compliance ensures adherence to laws. Integrating these enhances decision-making, efficiency, and business continuity while minimizing risks and regulatory issues.

The Risk Management Framework (RMF) integrates security, privacy, and cyber supply chain risk management into the system development life cycle. It follows a risk-based approach to control selection, considering legal, policy, and regulatory constraints. RMF applies to new and legacy systems across all technologies and organizations, ensuring effective information security and privacy management.

A risk assessment evaluates the likelihood, consequences, and tolerances of potential incidents. As part of a broader risk management strategy, it introduces control measures to mitigate risks. Its primary goal is to prevent negative outcomes or identify potential opportunities, ensuring effective decision-making and improved organizational resilience against uncertainties.

The AWS Well-Architected Framework helps assess whether a specific architecture aligns with cloud best practices. It provides a consistent approach to evaluating systems based on modern cloud standards and identifies necessary improvements. As AWS evolves, the framework is continually refined to incorporate learnings from customer experiences and advancements in cloud technology.

Governance, Risk, and Compliance (GRC) is a structured approach aligning IT and business goals while managing risks and meeting regulations. Governance sets policies and accountability, risk management identifies and mitigates threats, and compliance ensures adherence to laws. Integrating these enhances decision-making, efficiency, and business continuity while minimizing risks and regulatory issues.

The Risk Management Framework (RMF) integrates security, privacy, and cyber supply chain risk management into the system development life cycle. It follows a risk-based approach to control selection, considering legal, policy, and regulatory constraints. RMF applies to new and legacy systems across all technologies and organizations, ensuring effective information security and privacy management.

A risk assessment evaluates the likelihood, consequences, and tolerances of potential incidents. As part of a broader risk management strategy, it introduces control measures to mitigate risks. Its primary goal is to prevent negative outcomes or identify potential opportunities, ensuring effective decision-making and improved organizational resilience against uncertainties.

The AWS Well-Architected Framework helps assess whether a specific architecture aligns with cloud best practices. It provides a consistent approach to evaluating systems based on modern cloud standards and identifies necessary improvements. As AWS evolves, the framework is continually refined to incorporate learnings from customer experiences and advancements in cloud technology.

The Modernizing Government Technology (MGT) Act is a new federal act that mandates federal agencies to accelerate their IT modernization efforts. The act allows agencies to reprogram unused budget allocation to fund future IT modernization projects. It also updates the uses of the Technology Modernization Fund (TMF) to pay for retiring and replacing older information technology (IT) systems.

The Modernizing Government Technology Act reforms and reauthorizes the Technology Modernization Fund (TMF) and its governing board, the Technology Modernization Board (TMB), which were established by the bipartisan Modernizing Government Technology Act of 2017 (P.L. 115-91). The bill includes several measures to improve the administration of the TMF and ensure program operations adhere to original congressional intent. The bill requires TMF awards to be reimbursed at the level needed to ensure the Fund is operational and creates a new requirement that agency’s reimburse administrative fees. The bill also establishes a Federal Legacy IT Inventory, a new oversight tool that will allow Congress to evaluate agency and government-wide priority items for legacy IT modernization and to assess how well the TMF does in funding these projects. Finally, this bill reauthorizes the TMF and TMB and establishes a December 2031 sunset.

Operational Technology (OT) cybersecurity focuses on protecting the hardware and software that manage and control physical devices and processes in industrial environments.
Key aspects of OT cybersecurity include:

Transform data into actionable insights with advanced analytics and data governance solutions that drive informed decision-making.
An enterprise data architecture framework (EDAF) is a structured approach to managing and organizing data within an organization. It encompasses the entire data lifecycle, from collection and storage to processing and analysis.

FISMA compliance refers to adhering to a set of policies, standards, and guidelines to protect government information and systems. It is mandatory for federal agencies and their contractors. The key steps to achieve FISMA compliance include:

A Technology Roadmap is a strategic plan that outlines the technology initiatives an organization plans to undertake over a specific timeframe. It helps align technology projects with business goals, ensuring that all stakeholders understand the “what”, “why”, and “when” of IT initiatives.
Here are some key benefits of a Technology Roadmap:

Product vision – Describes the desired future state of the product and guides Agile ARTs and teams toward a common goal.
Product strategy – Defines how the organization will deliver against the product vision, providing clear direction while retaining the agility needed to evolve based on feedback and market conditions.
Product design – Combines customer centricity, design thinking, and lean user experience (lean UX) design to understand the problem to be solved deeply and discover solutions with the best product-market fit.
Product delivery – Accelerates value realization by ensuring that new ideas flow quickly from idea to impact through a Continuous Delivery Pipeline.
Product marketing – Raises awareness and excitement in the market by amplifying the features and benefits of product innovations.
Product innovation culture – Fosters continuous learning, experimentation, and a spirit of relentless improvement across the organization.
© Scaled Agile, Inc.

The NIST Zero Trust Architecture (ZTA) is a cybersecurity framework that emphasizes the principle of "never trust, always verify." It focuses on securing resources, users, and assets by assuming no implicit trust based on network location or ownership. You can explore the official NIST publication on Zero Trust Architecture here. Additionally, you might find a detailed guide and diagram in the NIST Special Publication 800-207.

FISMA compliance refers to adhering to a set of policies, standards, and guidelines to protect government information and systems. It is mandatory for federal agencies and their contractors. The key steps to achieve FISMA compliance include:

A Technology Roadmap is a strategic plan that outlines the technology initiatives an organization plans to undertake over a specific timeframe. It helps align technology projects with business goals, ensuring that all stakeholders understand the “what”, “why”, and “when” of IT initiatives.
Here are some key benefits of a Technology Roadmap:

Product vision – Describes the desired future state of the product and guides Agile ARTs and teams toward a common goal.
Product strategy – Defines how the organization will deliver against the product vision, providing clear direction while retaining the agility needed to evolve based on feedback and market conditions.
Product design – Combines customer centricity, design thinking, and lean user experience (lean UX) design to understand the problem to be solved deeply and discover solutions with the best product-market fit.
Product delivery – Accelerates value realization by ensuring that new ideas flow quickly from idea to impact through a Continuous Delivery Pipeline.
Product marketing – Raises awareness and excitement in the market by amplifying the features and benefits of product innovations.
Product innovation culture – Fosters continuous learning, experimentation, and a spirit of relentless improvement across the organization.
© Scaled Agile, Inc.

The NIST Zero Trust Architecture (ZTA) is a cybersecurity framework that emphasizes the principle of "never trust, always verify." It focuses on securing resources, users, and assets by assuming no implicit trust based on network location or ownership. You can explore the official NIST publication on Zero Trust Architecture here. Additionally, you might find a detailed guide and diagram in the NIST Special Publication 800-207.

The Modernizing Government Technology (MGT) Act is a new federal act that mandates federal agencies to accelerate their IT modernization efforts. The act allows agencies to reprogram unused budget allocation to fund future IT modernization projects. It also updates the uses of the Technology Modernization Fund (TMF) to pay for retiring and replacing older information technology (IT) systems.

The Modernizing Government Technology Act reforms and reauthorizes the Technology Modernization Fund (TMF) and its governing board, the Technology Modernization Board (TMB), which were established by the bipartisan Modernizing Government Technology Act of 2017 (P.L. 115-91). The bill includes several measures to improve the administration of the TMF and ensure program operations adhere to original congressional intent. The bill requires TMF awards to be reimbursed at the level needed to ensure the Fund is operational and creates a new requirement that agency’s reimburse administrative fees. The bill also establishes a Federal Legacy IT Inventory, a new oversight tool that will allow Congress to evaluate agency and government-wide priority items for legacy IT modernization and to assess how well the TMF does in funding these projects. Finally, this bill reauthorizes the TMF and TMB and establishes a December 2031 sunset.

Operational Technology (OT) cybersecurity focuses on protecting the hardware and software that manage and control physical devices and processes in industrial environments.
Key aspects of OT cybersecurity include:

Transform data into actionable insights with advanced analytics and data governance solutions that drive informed decision-making.
An enterprise data architecture framework (EDAF) is a structured approach to managing and organizing data within an organization. It encompasses the entire data lifecycle, from collection and storage to processing and analysis.

FISMA compliance refers to adhering to a set of policies, standards, and guidelines to protect government information and systems. It is mandatory for federal agencies and their contractors. The key steps to achieve FISMA compliance include:

A Technology Roadmap is a strategic plan that outlines the technology initiatives an organization plans to undertake over a specific timeframe. It helps align technology projects with business goals, ensuring that all stakeholders understand the “what”, “why”, and “when” of IT initiatives.
Here are some key benefits of a Technology Roadmap:

Product vision – Describes the desired future state of the product and guides Agile ARTs and teams toward a common goal.
Product strategy – Defines how the organization will deliver against the product vision, providing clear direction while retaining the agility needed to evolve based on feedback and market conditions.
Product design – Combines customer centricity, design thinking, and lean user experience (lean UX) design to understand the problem to be solved deeply and discover solutions with the best product-market fit.
Product delivery – Accelerates value realization by ensuring that new ideas flow quickly from idea to impact through a Continuous Delivery Pipeline.
Product marketing – Raises awareness and excitement in the market by amplifying the features and benefits of product innovations.
Product innovation culture – Fosters continuous learning, experimentation, and a spirit of relentless improvement across the organization.
© Scaled Agile, Inc.

The NIST Zero Trust Architecture (ZTA) is a cybersecurity framework that emphasizes the principle of "never trust, always verify." It focuses on securing resources, users, and assets by assuming no implicit trust based on network location or ownership. You can explore the official NIST publication on Zero Trust Architecture here. Additionally, you might find a detailed guide and diagram in the NIST Special Publication 800-207.

Stay ahead of the curve!—follow and subscribe to our social media channels below to remain digitally engaged.
Maryland (MD) MBE/WBE/ACDBE/ SBE/DBE/SBR/ # 23-293




MD TEDCO #T031304062412
MD IT Reseller #19674498
Virgina (NOVA) –


GSA Schedule 70 –
© 2025 EAMC – Managed. Secured. Assured. All rights reserved.

The Zachman Framework organizes enterprise architecture using a Two-Dimensional Classification Schema, with six interrogatives (What, How, When, Who, Where, Why) in a 6x6 Matrix Structure. It serves as an Enterprise Ontology, defining essential components, but is Not a Methodology, focusing on structuring architectural artifacts rather than guiding implementations.

TOGAF (The Open Group Architecture Framework) is a globally recognized enterprise architecture credential. It provides a structured approach to designing, planning, implementing, and governing IT architecture. TOGAF follows a high-level design approach, modeled at four levels: Business, Application, Data, and Technology, emphasizing modularization, standardization, and leveraging proven technologies and products.

Enterprise architecture consists of four key components: Business Architecture, defining roles, processes, and objectives; Data Architecture, managing the information used for operations; Application Architecture, overseeing software applications processing data; and Technology Architecture, supporting all layers with hardware and communication technology. Together, these components ensure efficient, structured, and scalable business operations.

The Department of Defense Architecture Framework (DODAF) is a comprehensive framework used by the U.S. DoD to develop and manage enterprise architectures. It provides a structured approach for representing and visualizing DoD systems, ensuring all stakeholders have a clear, consistent understanding of system structure and behavior for effective decision-making and operations.

Governance, Risk, and Compliance (GRC) is a structured approach aligning IT and business goals while managing risks and meeting regulations. Governance sets policies and accountability, risk management identifies and mitigates threats, and compliance ensures adherence to laws. Integrating these enhances decision-making, efficiency, and business continuity while minimizing risks and regulatory issues.

The Risk Management Framework (RMF) integrates security, privacy, and cyber supply chain risk management into the system development life cycle. It follows a risk-based approach to control selection, considering legal, policy, and regulatory constraints. RMF applies to new and legacy systems across all technologies and organizations, ensuring effective information security and privacy management.

Enter your content here. This area supports rich text formatting.

The AWS Well-Architected Framework helps assess whether a specific architecture aligns with cloud best practices. It provides a consistent approach to evaluating systems based on modern cloud standards and identifies necessary improvements. As AWS evolves, the framework is continually refined to incorporate learnings from customer experiences and advancements in cloud technology.

Operational Technology (OT) cybersecurity focuses on protecting the hardware and software that manage and control physical devices and processes in industrial environments.
Key aspects of OT cybersecurity include:

Transform data into actionable insights with advanced analytics and data governance solutions that drive informed decision-making.
An enterprise data architecture framework (EDAF) is a structured approach to managing and organizing data within an organization. It encompasses the entire data lifecycle, from collection and storage to processing and analysis.

The NIST Zero Trust Architecture (ZTA) is a cybersecurity framework that emphasizes the principle of "never trust, always verify." It focuses on securing resources, users, and assets by assuming no implicit trust based on network location or ownership. You can explore the official NIST publication on Zero Trust Architecture here. Additionally, you might find a detailed guide and diagram in the NIST Special Publication 800-207.

A Technology Roadmap is a strategic plan that outlines the technology initiatives an organization plans to undertake over a specific timeframe. It helps align technology projects with business goals, ensuring that all stakeholders understand the “what”, “why”, and “when” of IT initiatives.
Here are some key benefits of a Technology Roadmap:

The Modernizing Government Technology (MGT) Act is a new federal act that mandates federal agencies to accelerate their IT modernization efforts. The act allows agencies to reprogram unused budget allocation to fund future IT modernization projects. It also updates the uses of the Technology Modernization Fund (TMF) to pay for retiring and replacing older information technology (IT) systems.

Product vision – Describes the desired future state of the product and guides Agile ARTs and teams toward a common goal.
Product strategy – Defines how the organization will deliver against the product vision, providing clear direction while retaining the agility needed to evolve based on feedback and market conditions.
Product design – Combines customer centricity, design thinking, and lean user experience (lean UX) design to understand the problem to be solved deeply and discover solutions with the best product-market fit.
Product delivery – Accelerates value realization by ensuring that new ideas flow quickly from idea to impact through a Continuous Delivery Pipeline.
Product marketing – Raises awareness and excitement in the market by amplifying the features and benefits of product innovations.
Product innovation culture – Fosters continuous learning, experimentation, and a spirit of relentless improvement across the organization.
© Scaled Agile, Inc.

The Modernizing Government Technology Act reforms and reauthorizes the Technology Modernization Fund (TMF) and its governing board, the Technology Modernization Board (TMB), which were established by the bipartisan Modernizing Government Technology Act of 2017 (P.L. 115-91). The bill includes several measures to improve the administration of the TMF and ensure program operations adhere to original congressional intent. The bill requires TMF awards to be reimbursed at the level needed to ensure the Fund is operational and creates a new requirement that agency’s reimburse administrative fees. The bill also establishes a Federal Legacy IT Inventory, a new oversight tool that will allow Congress to evaluate agency and government-wide priority items for legacy IT modernization and to assess how well the TMF does in funding these projects. Finally, this bill reauthorizes the TMF and TMB and establishes a December 2031 sunset.

FISMA compliance refers to adhering to a set of policies, standards, and guidelines to protect government information and systems. It is mandatory for federal agencies and their contractors. The key steps to achieve FISMA compliance include: